Security News

Security analysts have observed three new versions of Prilex PoS-targeting malware this year, indicating that its authors and operators are back in action. Prilex started as ATM-focused malware in 2014 and it pivoted to PoS devices in 2016.

The latest Internet Security Report from the WatchGuard Threat Lab shows a reduction in overall malware detections from the peaks seen in the first half of 2021, along with an increase in threats for Chrome and Microsoft Office and the ongoing Emotet botnet resurgence. "While overall malware attacks in Q2 fell off from the all-time highs seen in previous quarters, over 81% of detections came via TLS encrypted connections, continuing a worrisome upward trend," said Corey Nachreiner, CSO at WatchGuard.

A quickly expanding botnet called Chaos is targeting and infecting Windows and Linux devices to use them for cryptomining and launching DDoS attacks. Even though it mainly propagates by attacking devices unpatched against various security vulnerabilities and SSH brute-forcing, Chaos will also use stolen SSH keys to hijack more devices.

Chaos, new multipurpose malware written in the Go programming language, is spreading across the world. The prevalence of malware written in Go has increased dramatically in recent years due to the language's flexibility, low antivirus detection rates and difficulty to reverse-engineer, Black Lotus Labs analysts noted.

A new, multi-functional Go-based malware dubbed Chaos has been rapidly growing in volume in recent months to ensnare a wide range of Windows, Linux, small office/home office routers, and enterprise servers into its botnet. "Chaos functionality includes the ability to enumerate the host environment, run remote shell commands, load additional modules, automatically propagate through stealing and brute-forcing SSH private keys, as well as launch DDoS attacks," researchers from Lumen's Black Lotus Labs said in a write-up shared with The Hacker News.
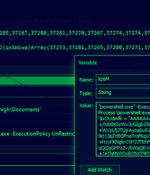
A recently discovered malware builder called Quantum Builder is being used to deliver the Agent Tesla remote access trojan. Sold on the dark web for €189 a month, Quantum Builder is a customizable tool for generating malicious shortcut files as well as HTA, ISO, and PowerShell payloads to deliver next-stage malware on the targeted machines, in this case Agent Tesla.

The Russian state-sponsored threat actor known as APT28 has been found leveraging a new code execution method that makes use of mouse movement in decoy Microsoft PowerPoint documents to deploy malware. "The code execution runs a PowerShell script that downloads and executes a dropper from OneDrive."

A new malware dropper named 'NullMixer' is infecting Windows devices with a dozen different malware families simultaneously through fake software cracks promoted on malicious sites in Google Search results. NullMixer acts as an infection funnel, using a single Windows executable to launch a dozen different malware families, leading to over two dozen infections running a single device.

The North Korean Lazarus hacking group is now using fake 'Crypto.com' job offers to hack developers and artists in the crypto space, likely with a long-term goal of stealing digital assets and cryptocurrency. In August 2022, Lazarus was seen targeting IT workers with malicious job offers that impersonated Coinbase and targeted users with Windows malware or macOS malware.
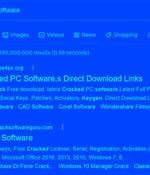
Cybercriminals are continuing to prey on users searching for cracked software by directing them to fraudulent websites hosting weaponized installers that deploy malware called NullMixer on compromised systems. "When a user extracts and executes NullMixer, it drops a number of malware files to the compromised machine," cybersecurity firm Kaspersky said in a Monday report.