Security News

The BlackCat ransomware gang, also known as ALPHV, has allegedly broken into IT firm NJVC, a provider of services to civilian US government agencies and the Department of Defense. DarkFeed, which monitors the dark web for ransomware intelligence, tweeted this week that BlackCat had added NJVC to its victims' list, along with sharing a screenshot allegedly of ALPHV's blog notifying NJVC that it had stolen data during its intrusion.
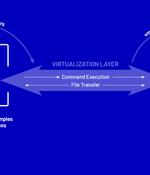
Threat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems and evade detection. Google's Mandiant threat intelligence division referred to it as a "Novel malware ecosystem" that impacts VMware ESXi, Linux vCenter servers, and Windows virtual machines, allowing attackers to maintain persistent access to the hypervisor as well as execute arbitrary commands.

Unknown attackers wielding novel specialized malware have managed to compromise VMware ESXi hypervisors and guest Linux and Windows virtual machines, Mandiant threat analysts have discovered. VirtualGATE is a utility program that incorporates a memory-only dropper and a payload that can run commands from a hypervisor host on a guest virtual machine, or between guest virtual machines on the same hypervisor host.

An espionage-focused threat actor has been observed using a steganographic trick to conceal a previously undocumented backdoor in a Windows logo in its attacks against Middle Eastern governments. Symantec's latest analysis of attacks between February and September 2022, during which the group targeted the governments of two Middle Eastern countries and the stock exchange of an African nation, highlights the use of a new backdoor called Stegmap.
A social engineering campaign leveraging job-themed lures is weaponizing a years-old remote code execution flaw in Microsoft Office to deploy Cobalt Strike beacons on compromised hosts. "The payload discovered is a leaked version of a Cobalt Strike beacon," Cisco Talos researchers Chetan Raghuprasad and Vanja Svajcer said in a new analysis published Wednesday.

New Chaos malware spreads over multiple architectures. Chaos, in addition to being able to work on multiple platforms, has also been designed to use known vulnerabilities and brute force SSH. Lumen researchers assess that Chaos is an evolution from the DDoS malware Kaiji based on code and function overlaps.

Security researchers have discovered a malicious campaign by the 'Witchetty' hacking group, which uses steganography to hide a backdoor malware in a Windows logo. The group is also considered part of the TA410 operatives, previously linked to attacks against U.S. energy providers.
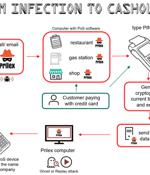
A Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to steal money by means of fraudulent transactions. "The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works," Kaspersky researchers said.

Hackers have found a new method to establish persistence on VMware ESXi hypervisors to control vCenter servers and virtual machines for Windows and Linux while avoiding detection.A modified level of trust is not enough for the ESXi system to accept it by default but the attacker also used the '-force' flag to install the malicious VIBs.

Emerging covert malware families that target VMware environments could allow criminals to gain persistent administrative access to the hypervisor, transfer files, and execute arbitrary commands between virtual machines, according to VMware and Mandiant, which discovered the software nasty earlier this year. Prior to this discovery, both VMware and Mandiant say they hadn't seen persistent malware with these capabilities deployed on VMware hypervisors or guest systems in the wild.