Security News

Google says that several state-backed hacking groups have joined ongoing attacks exploiting a high-severity vulnerability in WinRAR, a compression software used by over 500 million users, aiming to gain arbitrary code execution on targets' systems. Google's Threat Analysis Group, a team of security experts who defend Google users from state-sponsored attacks, has detected state hackers from several countries targeting the bug, including the Sandworm, APT28, and APT40 threat groups from Russia and China.

Interesting New York Times article about high-school students hacking the grading system. What's not helping? The policies many school districts are adopting that make it nearly impossible for low-performing students to fail-they have a grading floor under them, they know it, and that allows them to game the system.

A threat actor has leaked the complete source code for the first version of the HelloKitty ransomware on a Russian-speaking hacking forum, claiming to be developing a new, more powerful encryptor. A threat actor named Gookee has been previously associated with malware and hacking activity, attempting to sell access to Sony Network Japan in 2020, linked to a Ransomware-as-a-Service operation called 'Gookee Ransomware,' and trying to sell malware source code on a hacker forum.

Turns out pumps at gas stations are controlled via Bluetooth, and that the connections are insecure. No details in the article, but it seems that it's easy to take control of the pump and have it dispense gas without requiring payment.

The pitfalls of neglecting security ownership at the design stageIn this Help Net Security interview, Nima Baiati, Executive Director and GM, Commercial Cybersecurity Solutions at Lenovo, discusses the disconnect between development and security teams and how companies need to prioritize security and why utilizing a multi-layered strategy is the best way to secure above and below the OS. The hidden costs of neglecting cybersecurity for small businessesIn this Help Net Security interview, Raffaele Mautone, CEO of Judy Security, talks about the cybersecurity problems that small businesses face and the need for prioritization to save businesses from potential fines and damage to their brand reputation. Network Flight Simulator: Open-source adversary simulation toolNetwork Flight Simulator is a lightweight utility that generates malicious network traffic and helps security teams evaluate security controls and network visibility.

Cybersecurity agencies from Japan and the U.S. have warned of attacks mounted by a state-backed hacking group from China to stealthily tamper with branch routers and use them as jumping-off points...

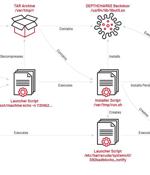
Initial access brokers are cybercriminals that focus on gaining privileged IT access to corporate environments, which they then auction off on specialized dark web forums. We wanted to better understand how IABs operate, so we did the only natural thing and spent weeks painstakingly translating posts from Russian into English to conduct an in-depth analysis on the corporate access economy.

Hackers are targeting Cisco Adaptive Security Appliance SSL VPNs in credential stuffing and brute-force attacks that take advantage of lapses in security defenses, such as not enforcing multi-factor authentication. Last week, BleepingComputer reported that the Akira ransomware gang was breaching Cisco VPNs for initial network access.

Data from the human vs. machine challenge could provide a framework for government and enterprise policies around generative AI. OpenAI, Google, Meta and more companies put their large language models to the test on the weekend of August 12 at the DEF CON hacker conference in Las Vegas. The Generative Red Team Challenge organized by AI Village, SeedAI and Humane Intelligence gives a clearer picture than ever before of how generative AI can be misused and what methods might need to be put in place to secure it.
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.