Security News

We don't know what we don't know; this is the quintessential problem plaguing security teams and the primary reason that zero-day exploits can cause such damage. With the element of surprise on an attacker's side, it can feel like security teams are at a total loss when it comes to these types of threats, but that doesn't mean there aren't steps that can be taken to prepare for such an attack.
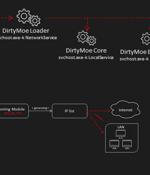
"The worming module targets older well-known vulnerabilities, e.g., EternalBlue and Hot Potato Windows privilege escalation," Avast researcher Martin Chlumecký said in a report published Wednesday. "One worm module can generate and attack hundreds of thousands of private and public IP addresses per day; many victims are at risk since many machines still use unpatched systems or weak passwords."

A new Linux botnet is using the infamous Log4j vulnerability to install rootkits and steal data. Researchers at Chinese internet security company Qihoo's 360's Network Security Research Lab discovered the botnet family, which they dubbed B1txor20, as it was infecting new hosts via the Log4j vulnerability.
First observed propagating through the Log4j vulnerability on February 9, 2022, the malware leverages a technique called DNS tunneling to build communication channels with command-and-control servers by encoding data in DNS queries and responses. B1txor20, while also buggy in some ways, currently supports the ability to obtain a shell, execute arbitrary commands, install a rootkit, open a SOCKS5 proxy, and functions to upload sensitive information back to the C2 server.

The newly found malware, dubbed B1txor20 by researchers at Qihoo 360's Network Security Research Lab, focuses its attacks on Linux ARM, X64 CPU architecture devices. The botnet uses exploits targeting the Log4J vulnerability to infect new hosts, a very appealing attack vector seeing that dozens of vendors use the vulnerable Apache Log4j logging library.

Researchers have disclosed a new technique that could be used to circumvent existing hardware mitigations in modern processors from Intel, AMD, and Arm and stage speculative execution attacks such as Spectre to leak sensitive information from host memory.Attacks like Spectre are designed to break the isolation between different applications by taking advantage of an optimization technique called speculative execution in CPU hardware implementations to trick programs into accessing arbitrary locations in memory and thus leak their secrets.

TLStorm exploits expose more than 20 million UPS units to takeover. The exploits come, said Armis head of research Barak Hadad, in a time when even the least likely of devices has an internet connection that turns it into a potential threat.

A new Linux vulnerability known as 'Dirty Pipe' allows local users to gain root privileges through publicly available exploits. Security researcher Phith0n illustrated how they could use the exploit to modify the /etc/passwd file so that the root user does not have a password.

The Log4Shell vulnerabilities in the widely used Log4j software are still leveraged by threat actors today to deploy various malware payloads, including recruiting devices into DDoS botnets and for planting cryptominers. The threat actor can then control this botnet to perform DDoS attacks against a specific target, depleting their resources and disrupting their online service.

An Iranian-aligned hacking group tracked as TunnelVision was spotted exploiting Log4j on VMware Horizon servers to breach corporate networks in the Middle East and the United States. Security analysts at SentinelLabs who have been tracking the activity chose that name due to the group's heavy reliance on tunneling tools, which help them hide their activities from detecting solutions.