Security News > 2022 > January

Week in review: PolKit vulnerability, fake tax apps pushing malware, EU’s bug bounty for open source
PolKit vulnerability can give attackers root on many Linux distrosA memory corruption vulnerability in PolKit, a component used in major Linux distributions and some Unix-like operating systems, can be easily exploited by local unprivileged users to gain full root privileges. Attackers connect rogue devices to organizations' network with stolen Office 365 credentialsAttackers are trying out a new technique to widen the reach of their phishing campaigns: by using stolen Office 365 credentials, they try to connect rogue Windows devices to the victim organizations' network by registering it with their Azure AD. Stealthy Excel malware putting organizations in crosshairs of ransomware gangsThe HP Wolf Security threat research team identified a wave of attacks utilizing Excel add-in files to spread malware, helping attackers to gain access to targets, and exposing businesses and individuals to data theft and destructive ransomware attacks.

A security researcher has publicly disclosed an exploit for a Windows local privilege elevation vulnerability that allows anyone to gain admin privileges in Windows 10. The vulnerability affects all supported support versions of Windows 10 before the January 2022 Patch Tuesday updates.

Researchers have found over 20,000 instances of publicly exposed data center infrastructure management software that monitor devices, HVAC control systems, and power distribution units, which could be used for a range of catastrophic attacks. Data centers house costly systems that support business storage solutions, operational systems, website hosting, data processing, and more.

The amount of time devices running Windows are powered on and connected to Windows Update is tracked by Microsoft as 'Update Connectivity. "One of the most impactful things we explored was how much time a device needs to be powered on and connected to Windows Update to be able to successfully install quality and feature updates," said Guyer.

Cybersecurity researchers on Tuesday took the wraps off a multi-stage espionage campaign targeting high-ranking government officials overseeing national security policy and individuals in the defense industry in Western Asia. Trellix attributed the attacks with moderate confidence to the Russia-based APT28 group, the threat actor behind the compromise of SolarWinds in 2020, based on similarities in the source code as well as in the attack indicators and geopolitical objectives.

As you probably know, PCR tests, which currently require processing in a laboratory, are considered more accurate than self-administered lateral flow tests. PCR tests are both advised and free in the UK if you already have coronavirus symptoms, or have been in contact with someone who's infectious.
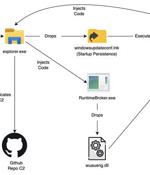
The notorious Lazarus Group actor has been observed mounting a new campaign that makes use of the Windows Update service to execute its malicious payload, expanding the arsenal of living-off-the-land techniques leveraged by the APT group to further its objectives. The Lazarus Group, also known as APT38, Hidden Cobra, Whois Hacking Team, and Zinc, is the moniker assigned to the North Korea-based nation-state hacking group that's been active since at least 2009.

An initial access broker group tracked as Prophet Spider has been linked to a set of malicious activities that exploits the Log4Shell vulnerability in unpatched VMware Horizon Servers. The payloads observed include cryptocurrency miners, Cobalt Strike Beacons, and web shells, corroborating a previous advisory from the U.K. National Health Service that sounded the alarm on active exploitation of the vulnerabilities in VMware Horizon servers to drop malicious web shells and establish persistence on affected networks for follow-on attacks.

New fossils from Newfoundland push the origins of cephalopods to 522 million years ago. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t...

It's been a busy week with ransomware attacks tied to political protests, new attacks on NAS devices, amazing research released about tactics, REvil's history, and more. A new DeadBolt ransomware group is encrypting QNAP NAS devices worldwide using what they claim is a zero-day vulnerability in the device's software.